How To Prevent A Distributed Denial Of Service Attack
A DDoS assault enables a hacker to flood a network or server with bogus traffic. Too much traffic overloads resources and disrupts connectivity, stopping the organisation from processing genuine user requests. Services become unavailable, and the target visitor suffers prolonged downtime, lost revenue, and dissatisfied customers. This commodity explains how a business can prevent DDoS attacks and stay a step alee of would-be hackers. The practices we testify below help minimize the impact of a DDoS and ensure a quick recovery from an attack attempt. A DDoS (Distributed Denial of Service) is a cyberattack that aims to crash a network, service, or server by flooding the organisation with imitation traffic. The sudden fasten in messages, connection requests, or packets overwhelms the target'south infrastructure and causes the system to slow down or crash. While some hackers apply DDoS attacks to bribery a business into paying a ransom (similar to ransomware), more than common motives behind a DDoS are to: DDoS attacks are a danger to businesses of all sizes, from Fortune 500 companies to small e-retailers. Statistically, DDoS hackers almost often target: Attackers typically use a botnet to crusade a DDoS. A botnet is a linked network of malware-infected computers, mobile devices, and IoT gadgets under the aggressor's command. Hackers use these "zombie" devices to send excessive numbers of requests to a target website or server'due south IP accost. Once the botnet sends enough requests, online services (emails, websites, spider web apps, etc.) slow down or fail. Co-ordinate to a Radware report, these are the average lengths of a DDoS assail: While a DDoS typically does not directly pb to a information breach or leakage, the victim spends time and coin getting services back online. Loss of business, abased shopping carts, frustrated users, and reputational impairment are usual consequences of failing to prevent DDoS attacks. A DDoS is often a lark for other, more disastrous threats. Read well-nigh the most unsafe cyber security assault types and learn how to protect your business. While all DDoS attacks aim to overwhelm a arrangement with likewise much action, hackers have unlike strategies they rely on to crusade a distributed deprival of service. The three primary types of attack are: The three approaches rely on different techniques, but a skilled hacker tin can utilize all three strategies to overwhelm a single target. All pNAP servers come up with DDoS protection at no additional cost. Stay online 24/7 with our automated traffic filtering and lightning-fast DDoS mitigation infrastructure. An application-layer attack targets and disrupts a specific app, not an entire network. A hacker generates a loftier number of HTTP requests that exhaust the target server'southward ability to respond. Cybersecurity specialists measure app-layer attacks in requests per second (RPS). Common targets of these attacks include: Trying to prevent DDoS attacks of this type is challenging as security teams often struggle to distinguish between legitimate and malicious HTTP requests. These attacks employ fewer resources than other DDoS strategies, and some hackers tin can even use but a unmarried device to orchestrate an application-layer attack. Another common proper noun for an app-level DDoS is a layer 7 attack. Protocol DDoS attacks (or network-layer attacks) exploit weaknesses in the protocols or procedures that govern internet communications. While an app-level DDoS targets a specific app, the goal of a protocol attack is to slow down the entire network. The ii most common types of protocol-based DDoS attacks are: Cybersecurity experts measure out protocol attacks in packets per second (PPS) or bits per second (BPS). The main reason why protocol DDoS is and then widespread is that these attacks tin can easily featherbed poorly configured firewalls. A volume-based DDoS set on consumes a target's available bandwidth with fake information requests and creates network congestion. The assaulter's traffic blocks legitimate users from accessing services, preventing traffic from flowing in or out. The most mutual types of volumetric DDoS attack types are: All volumetric attacks rely on botnets. Hackers use armies of malware-infected devices to cause traffic spikes and use up all available bandwidth. Volumetric attacks are the most common type of DDoS. Bare Metallic Cloud, pNAP's cloud-native defended server, offers a robust resistance to DDoS. Each server comes with free xx Gbps DDoS protection that ensures availability even if you face up a high-traffic volumetric assault. While there is no fashion to prevent a hacker from attempting to cause a DDoS, proper planning and proactive measures reduce the risk and potential impact of an attack. Your security team should develop an incident response programme that ensures staff members respond promptly and effectively in case of a DDoS. This plan should cover: The ability to react to unexpected events is vital to business continuity. Our article on disaster recovery takes you through all you lot need to know to create an effective DR plan. Network security is essential for stopping any DDoS attack attempt. As an assail only has an touch if a hacker has plenty time to pile up requests, the ability to identify a DDoS early on is vital to controlling the blast radius. You can rely on the post-obit types of network security to protect your business from DDoS attempts: Protecting from DDoS attacks also requires high levels of network infrastructure security. Securing networking devices enables you to set up your hardware (routers, load-balancers, Domain Proper name Systems (DNS), etc.) for traffic spikes. Relying on multiple distributed servers makes it hard for a hacker to set on all servers at the same time. If an attacker launches a successful DDoS on a unmarried hosting device, other servers remain unaffected and take on extra traffic until the targeted arrangement is back online. You should host servers at data centers and colocation facilities in unlike regions to ensure you do not have any network bottlenecks or single points of failure. You can also use a content commitment network (CDN). Since DDoS attacks work by overloading a server, a CDN can share the load equally across several distributed servers. PhoenixNAP's colocation services enable y'all to prepare an optimal hosting environment while enjoying pinnacle levels of security, high redundancy, and a variety of managed services. If your security team can chop-chop place the traits of a DDoS attack, you lot tin take timely action and mitigate the damage. Mutual signs of a DDoS are: Remember that not all DDoS attacks come with loftier traffic. A low-book assail with a short duration often goes under the radar equally a random outcome. However, these attacks can be a examination or diversion for a more dangerous breach (such every bit ransomware). Therefore, detecting a low-book attack is as vital as identifying a full-blown DDoS. Consider organizing a security awareness preparation program that educates the unabridged staff on the signs of a DDoS attack. That fashion, you exercise not demand to look for a security squad member to option upwardly on the warning signs. Using continuous monitoring (CM) to analyze traffic in existent-fourth dimension is an excellent method of detecting traces of DDoS activity. The benefits of CM are: Depending on a setup, the CM tool either contacts admins in case of an result or follow response instructions from a pre-defined script. Intrigued by continuous monitoring? Our Nagios tutorial explores this popular CM tool and offers an ideal starting point for newcomers to Nagios. A hacker behind a DDoS attack will likely send requests to every device on your network to amplify the bear upon. Your security squad can counter this tactic by limiting network broadcasting between devices. Limiting (or, where possible, turning off) broadcast forwarding is an effective style to disrupt a high-volume DDoS attempt. Where possible, yous can also consider instructing employees to disable repeat and chargen services. While using on-prem hardware and software to counter the DDoS threat is vital, cloud-based mitigation does non have the same capacity limitations. Deject-based protection can scale and handle even a major volumetric DDoS assail with ease. Y'all have the option of outsourcing DDoS prevention to a cloud provider. Some of the cardinal benefits of working with a third-party vendor are: A concern typically has 2 choices when setting up cloud-based DDoS protection: If your in-house team has the necessary know-how, you may not demand to solely rely on a cloud provider for deject-based DDoS protection. You can set up a hybrid or multi-deject environment and organize your traffic to get the same effects every bit either on-demand or e'er-on DDoS protection. DDoS threats are not only becoming more dangerous, but attacks are also increasing in number. Experts predict the boilerplate number of annual DDoS attempts will ascent to 15.4 meg past 2023. That number indicates that nearly every business will face a DDoS at some point, so preparing for this attack type should exist at the superlative of your security to-do list.
What Is a DDoS Attack?
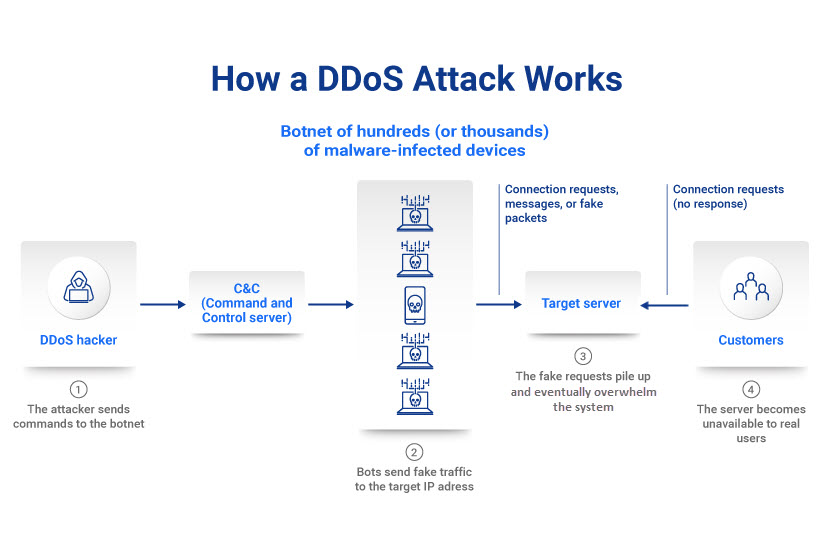
Types of DDoS Attacks
Awarding-Layer Attacks
Protocol Attacks
Volumetric Attacks
7 Best Practices to Prevent DDoS Attacks
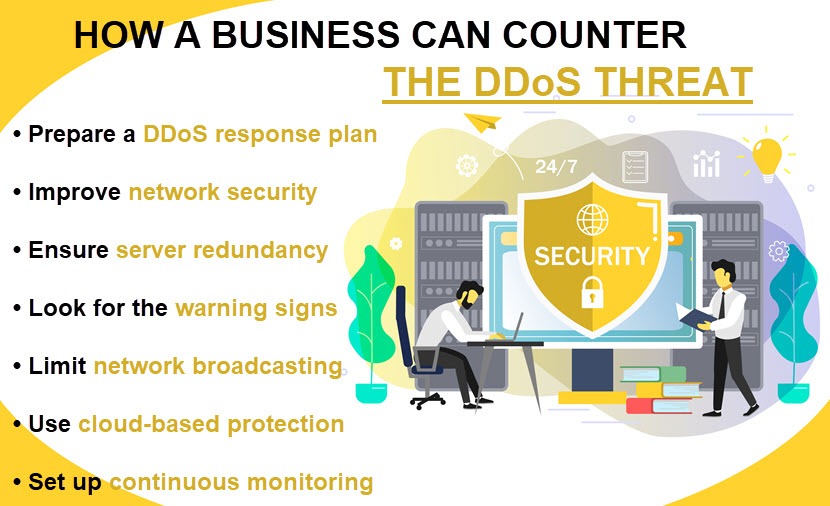
Create a DDoS Response Plan
Ensure High Levels of Network Security
Accept Server Back-up
Look Out for the Warning Signs

Continuous Monitoring of Network Traffic
Limit Network Broadcasting
Leverage the Cloud to Preclude DDoS Attacks
Do Not Overlook the DDoS Threat
How To Prevent A Distributed Denial Of Service Attack,
Source: https://phoenixnap.com/blog/prevent-ddos-attacks
Posted by: arellanothavent.blogspot.com


0 Response to "How To Prevent A Distributed Denial Of Service Attack"
Post a Comment